
Introduction

The digital revolution has ushered in an era of unparalleled connectivity — and unprecedented threats. Cybersecurity professionals are the vanguard against cybercrime, tasked with protecting sensitive data and critical infrastructures. This guide is your comprehensive roadmap to mastering cybersecurity, from foundational concepts to advanced specializations. Along the way, we’ll explore career prospects, typical job roles, certifications, and the years of experience needed to thrive in this field.
For better understanding you can go through these articles too :
1. nwkings.com/cyber-security-roadmap
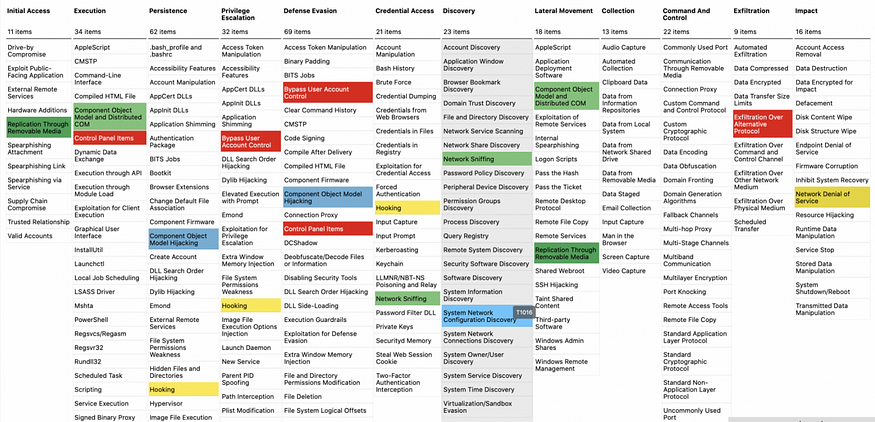
Phase 1: Laying the Foundation (Beginner Level)

1. Understand the Cyber Landscape
Learn the basics of cybersecurity: Malware, Phishing, and Password Attacks.
Gain a solid understanding of cybersecurity principles: threats, vulnerabilities, risk assessment, and mitigation strategies.
Stay updated on the latest cyber threats by following platforms like ThreatPost, DarkReading, and Hacker News.
Recommended Read: “The Art of Invisibility” by Kevin Mitnick.
2. Operating Systems & Networking Basics
Learn the basics of networking: TCP/IP, DNS, VPNs, and HTTP/HTTPS.
Familiarize yourself with tools like Wireshark to analyze network traffic.
Understand system fundamentals on both Linux and Windows, including PowerShell.
Certification: Start with CompTIA Network+.
3. Programming for Cybersecurity
Learn Python for scripting and penetration testing.
Master Bash scripting and SQL to understand and mitigate database vulnerabilities.
Typical Job Roles:
IT Support Specialist (0–2 years experience)
Junior Network Engineer (0–2 years experience)
Phase 2: Building Expertise (Intermediate Level)

4. Ethical Hacking & Penetration Testing
Use tools like Kali Linux, Metasploit, Nmap, and John the Ripper.
Practice the practical side of ethical hacking on platforms like TryHackMe and HackTheBox.
Certification: Aim for Certified Ethical Hacker (CEH) or eJPT (eLearnSecurity Junior Penetration Tester).
5. Web & Application Security
Study the OWASP Top 10 vulnerabilities and how to mitigate them.
Use tools like Burp Suite and OWASP ZAP for application security testing.
Certification: Consider GWAPT (GIAC Web Application Penetration Tester).
6. Cloud Security & DevSecOps
Learn to secure cloud platforms like AWS, Azure, and Google Cloud.
Explore container security with Docker and Kubernetes.
Understand CI/CD pipeline security and Infrastructure-as-Code (IaC) using Terraform.
Typical Job Roles:
Cybersecurity Analyst (2–4 years experience)
Penetration Tester (2–4 years experience)
Cloud Security Engineer (3–5 years experience)
Phase 3: Mastery and Specialization (Expert Level)

7. Digital Forensics & Incident Response (DFIR)
Use tools like Autopsy, Volatility, and Splunk for incident analysis and response.
Develop skills in real-time threat hunting and log analysis.
Certification: GCFA (GIAC Certified Forensic Analyst) or CHFI (Certified Hacking Forensic Investigator).
8. Red Team vs. Blue Team Operations
Red Team: Hone offensive security skills, including social engineering and penetration testing.
Blue Team: Focus on defensive tactics, threat hunting, and SOC operations.
Leverage the MITRE ATT&CK framework to simulate real-world attacks.
Certification: OSCP (Offensive Security Certified Professional) for Red Team and GCIH (GIAC Certified Incident Handler) for Blue Team.
9. Bug Bounty Programs & Real-World Experience
Join platforms like HackerOne and Bugcrowd to identify and report vulnerabilities.
Study public bug disclosure reports to understand professional workflows.
Typical Job Roles:
Security Architect (5–7 years experience)
Incident Response Manager (6–8 years experience)
Red Team Lead or Blue Team Lead (7–10 years experience)
Certifications for Cybersecurity Professionals

Here’s a list of essential certifications to boost your career:
Entry-Level:
CompTIA Security+
CompTIA Network+
eJPT (eLearnSecurity Junior Penetration Tester)
Intermediate:
CEH (Certified Ethical Hacker)
OSCP (Offensive Security Certified Professional)
CISSP (Certified Information Systems Security Professional)
Advanced:
GCFA (GIAC Certified Forensic Analyst)
GCIH (GIAC Certified Incident Handler)
CISM (Certified Information Security Manager)
CHFI (Certified Hacking Forensic Investigator)
Career Prospects: Cybersecurity Job Roles & Growth Path

Entry-Level Roles (0–2 Years)
IT Support Specialist
Junior Cybersecurity Analyst
Mid-Level Roles (2–5 Years)
Penetration Tester
Threat Intelligence Analyst
Cloud Security Engineer
Advanced Roles (5+ Years)
Cybersecurity Manager
Security Architect
Incident Response Leader
Executive Roles (10+ Years)
Chief Information Security Officer (CISO)
Director of Cybersecurity
Conclusion

Cybersecurity is more than just a career — it’s a mission. From safeguarding networks to leading response teams, every role contributes to the fight against cybercrime. By following this roadmap and earning relevant certifications, you’ll gain both the technical skills and strategic mindset to excel. Whether you aim to be an ethical hacker, a forensic investigator, or a CISO, this guide will help you defend, detect, and dominate in the field of cybersecurity. Ready to embark on this thrilling journey? The future of cybersecurity awaits!
Thank you for taking the time to read my blog. Your feedback is immensely valuable to me. Please feel free to share your thoughts and suggestions.
